Offensive Security Certified Professional (OSCP), 07/1/22
The Course:
PEN-200 is by far one of the most interesting courses I’ve taken.
I got first hand instruction on how bad actors carry out many different kinds of attacks from misconfigured snmp services, stacked query/nosql injections, and poisoned MS Office Macros, to pivoting in an Active Directory environment.
Their are so many tricks I learned in the course but honestly the most essential I learned of them all is enumeration. The ability to effectively enumerate the attack surface really is the difference between finding a vector to attack or not finding a vector to attack.
I took PEN-200 after offsec added the Active directory portion to the exam. The previous exam consisted of 5 independent machines, so there was no element of tunneling involved. Additionally, the Active Directory portion of the exam is 40 points all or nothing, meaning a student either compromises the entire domain and earns the full 40 points or a student partially compromises the domain and earns 0 points. I suspect this is why many people have said made the exam more difficulty.
In my four years computer science education, two of which were at the University of California Santa Cruz, I never touched upon the concepts of tunneling, proxy servers, or modern directory services infrastracture.
However I did gain the ability to read and write code in multiple programming languages, which comes in handy when debugging an exploit written by someone else, and provides a good understanding of network protocols such as HTTP/s, SOAP, etc.
For me completing this course was a milestone on my journey towards becoming a pentester.
The Lab:
Around the same time that Offsec changed the structure of the exam, they released some data which basically detailed the correlation between the number of lab machines a student completes and the passing rates of the exam itself.
For reference the image is below.
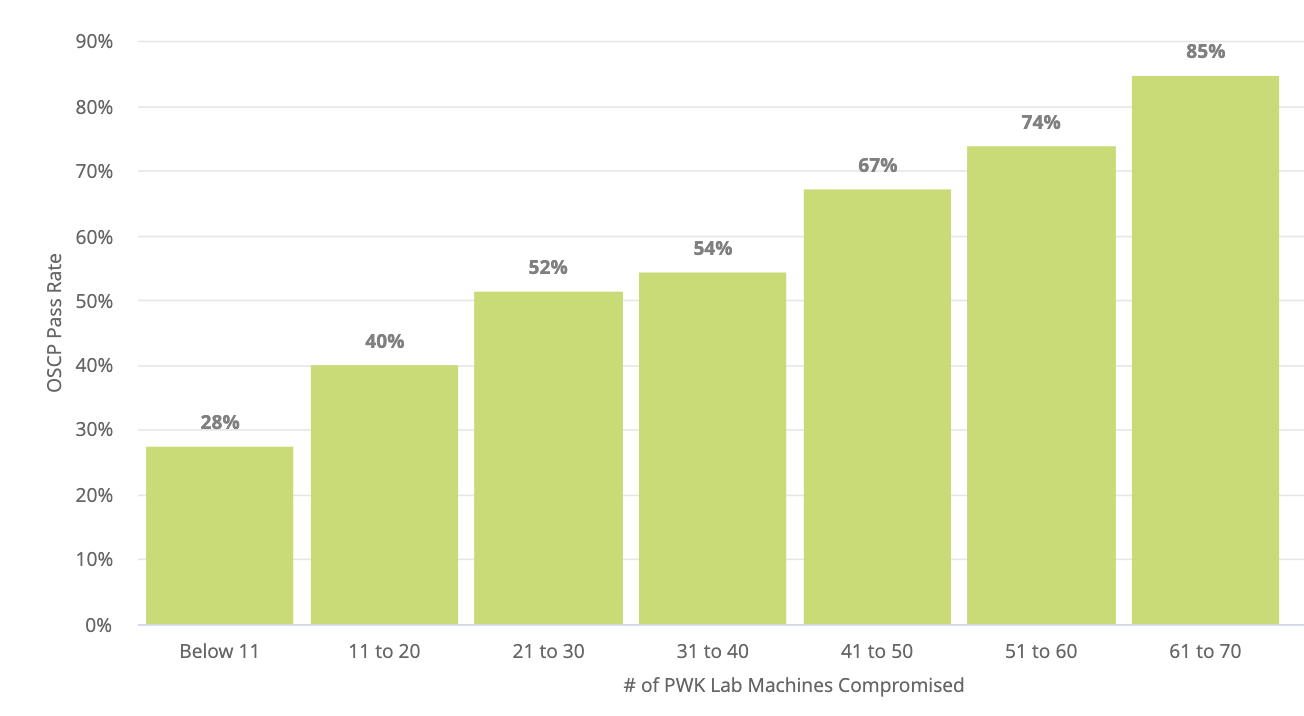 PWK Correlation (NOT CAUSATION!) between lab machines completed and OSCP exam pass rates
It seems rather obvious that completing a large number of lab machines is highly correlated with passing.
PWK Correlation (NOT CAUSATION!) between lab machines completed and OSCP exam pass rates
It seems rather obvious that completing a large number of lab machines is highly correlated with passing.
Coming from an engineering background I knew that, in order to not disappoint myself, I really had no choice other than to hack every machine in the PEN-200 labs which I did.
By the time I finished all of the PEN-200 lab machines I felt offsec had done a good job of introducing the different classes of vulnerabilites
you might encounter in a network pentest. It was an approach that focused on breadth rather than depth.
I honestly felt pretty decently prepared for the exam.
I’d highly recommend proving grounds practice as supplemental material to anyone who is taking PEN-200.
There was also some hack the box machines that were pretty good BUT there were more than a few (and this is the same reason I don’t recommend proving grounds play) that had weird stuff as initial footholds. For instance a plaintext password set in the description of a user object in ldap or a base64 encoded ssh password in the text of a web page. I didn’t encounter anything like that in proving grounds practice. One of the machines I’d recommend is squid, SE impersonate is something we can give ourselves!
The Exam:
While I can’t discuss the specifics of the exam,
I don’t think there is anything that I encountered on the exam that was not in the PEN-200 labs in one form or another.
For reference I scored 80 points on the exam.
The labs did a great job of introducing many different kinds of services thereby forcing you to learn how to enumerate each of them.
The Certification:
Earning the certificate was a great feeling because it validated my experiences throught the PEN-200 labs.
 My Certificate
My Certificate




